stSoftware blog

How are SQL Injection attacks prevented?
14 Mar 2014
SQL injection is a code injection technique, used to attack data driven applications like stSoftware. stSoftware systems support a number of web accessible protocols including:- ReST SOAP Web Forms GWT RPC All protocols access the underlying data through the DAL ( data access layer). There is NO direct access to the underlying data store no matter which protocol is used. Each protocol accepts the request to read or write data and then perform the protocols validations and then passes the request...
Read More
How can stSoftware's CMS be used to manage events and resources?
13 Mar 2014
Events and Resources are managed through multiple Modules. They are briefly outlined here; Events Details, site, time and date, duration Invite attendees – select attendees then click send invitation button to send template email to all attendees & record status and attendance Scheduler scheduling events - resources according to availability, skill set, location Admin manage staff resources – availability rules, specialisations and rates Timeline Easy graphical interface for tasks, events, jobs (...
Read MoreExporting Reports to PDF and Excel
11 Mar 2014
Click on the Export button and then choose the file format of your choice: CSV, PDF or Spreadsheet (EXCEL) Marking the records by clicking on the left hand checkbox, will export only the selected records.
Read More
New template "Munter"
7 Mar 2014
A new template "Munter" has been added to our Content Management System (CMS). Munter is a very handsome Bootstrap 3 theme. Comes with beautiful features like a fixed arrows navigation, a nice portfolio showcase and a smooth scroll. Sections:- Home About Articles Mission People Contact All site details can be updated via the site wizard Home page - mobile
Read More
What is the recommended upgrade schedule for self hosted systems?
4 Mar 2014
We recommend at least quarterly maintenance release are installed to your test environment, tested then promoted to your production system as part of the normal software maintenance cycle. Regular and timely updates reduce the risks of running a live system that is out of sync with stSoftware's current version and enables your users to benefit from our R&D program, which is our investment and commitment to continually improve our systems for our customers (in recent years we have typically invested...
Read More
Windows Active Directory Single Sign-on for stSoftware servers
2 Mar 2014
Overview Single sign using Microsoft LAN Manager (NTLM) allows users within a intranet enviroment to use the system without the need to re-enter their password once they have logged into the Windows network. Note the NTLM protocol can only be used within a internet environment. Configuration Within a Windows intranet environment . Multiple options available within the The system has a environment variable “SSO_DISABLE” which can be used to completely disable Single Sign On for a server. Each layer... * * If disabled at the * Signal Sign On modes * 1) TRANSPARENT - only transparent login * 2) HYBRID - Transparent or database password. * * @param layer the layer * @param userModeSSO user wants to enable SSO * @return true if enabled. * @throws Exception a serious problem. */ public static String ssoMode( final VirtualDB layer, final String userModeSSO) throws Exception { DBSysPrefs sysPrefs = layer.getGlobalObject().getSysPrefs(); String ssoDisable= sysPrefs.getString( DBSysPrefs.DBFIELD_SSO_DISABLE); if( "yes".equalsIgnoreCase(ssoDisable) || "true".equalsIgnoreCase(ssoDisable)) { return ""; } if( MODE_HYBRID.equalsIgnoreCase(userModeSSO) ) { return MODE_HYBRID; } else if( MODE_TRANSPARENT.equalsIgnoreCase(userModeSSO) ) { return MODE_TRANSPARENT; } else if( "false".equalsIgnoreCase(userModeSSO) ) { return ""; } else if( StringUtilities.isBlank(userModeSSO) == false) { LOGGER.warn("invalid SSO user mode: " + userModeSSO ); } String layerModeSSO= sysPrefs.getString( DBSysPrefs.DBFIELD_SSO_MODE); if( MODE_HYBRID.equalsIgnoreCase(layerModeSSO) ) { return MODE_HYBRID; } else if( MODE_TRANSPARENT.equalsIgnoreCase(layerModeSSO) ) { return MODE_TRANSPARENT; } else if( StringUtilities.isBlank(layerModeSSO) == false) { LOGGER.warn("invalid SSO layer mode: " + layerModeSSO ); } return ""; } If the SSO mode is calculated to be “HYBRID” then the user's browser will be redirected to a protected page on the IIS server. The protected page on the IIS server will cause the user to authenticated via NTML. Once the user is authenticated the user details are encrypted with a private key known as a “shared secret” and then these encrypted details are re-directed back to the calling webserver. The calling webserver decrypts the user details using the “shared secret” private key. If the authentication...
Read More
New template "Grayscale"
28 Feb 2014
A new template "grayscale" has been added to our Content Management System (CMS). This template is a fully functional, premium quality Bootstrap theme. It includes the following features: Easing scroll function for smooth navigation Fully Functional, home + 3 pages Website Home About Mission Contact Google Map of your office location All site details can be updated via the site wizard Home page - mobile Contact page-iPad
Read More
New template "Business Casual"
26 Feb 2014
The Content Management System (CMS) contains a new template "Business Casual" Fully Functional, 4 Page Website: Home About Blog Contact Integrated article modules Bootstrap Carousel Built-In for the lastest published articles. Google Map of your office location All site details can be updated via the site wizard Home page Desktop About page Blog page Contact page
Read More
Site Wizard can create a professional site in minutes.
26 Feb 2014
Our site wizard is a simple way to get a professional website Simply click on the wizard, enter your company details into the form provided and your information will automatically populate the pre-designed website template of your choice, giving you a quality website in minutes. You can choose to use this website, change the template, or tweak it to your hearts content, our system is accommodating and easy to use. There are a number of pre-designed site templates included in the base system. Open...
Read More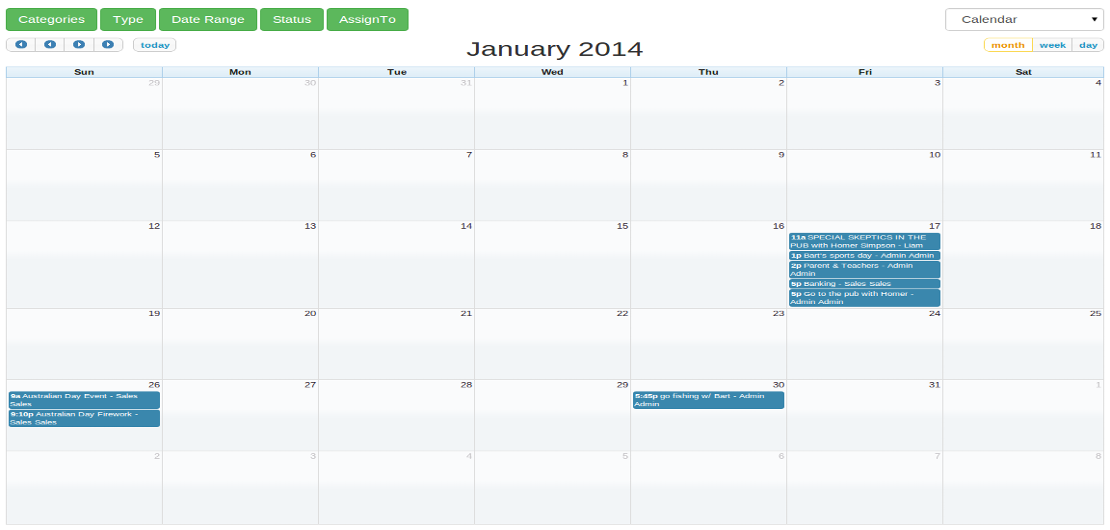
What is the new Calendar?
18 Feb 2014
The new Calendar is a full-sized, drag & drop calendar. It uses AJAX to fetch events on-the-fly for each month/week/day. Select from the filters to change the date range and items displayed according to type, category, status and assign to. Items are tasks, events, sales opportunities or jobs which have been entered and scheduled to a day and time. You'll see items in the calendar. Click on the item to see the details of the item. You can switch between the calendar and timeline view any time. We...
Read More
How to dynamically resize images on the server side?
31 Jan 2014
Overview The download of large images to the client browser which will be later resized to be a smaller image is very wasteful and slow. Let the server dynamically resize and cache your images with NO overhead to subsequent calls. To use in your HTML just add the desired behaviour to the URL e.g "?max-width=100" Available image transformations The sample large image is a landscape image of 1,000px × 667px which is 1.1m in size. You can resize the image while maintaining the same aspect ratio. The...
Read More
What is the recommended configuration for a Linux server?
26 Jan 2014
Overview All Linux servers are locked down to the highest security standards possible. All services are off by default and all ports shut. Only the required services started. To lock down a server:- Install and run only the services you require. Block all ports by default and open only those that are required Run servers as low permission user Disable direct login to ROOT completely. Block SSH login attempts from unknown locations and machines. Set up tripwire to detect intrusions Increase file ... sudo ufw allow imap sudo ufw allow http sudo ufw allow https sudo ufw disable sudo ufw enable Redirect the high permission ports 80 (http) and 443 (https) up to a port range that can accessed by the low permission user running the web service. Redirection of the ports can be done by the following iptable rules -A PREROUTING -p tcp -m tcp --dport 80 -j REDIRECT --to-ports 8080 -A PREROUTING -p tcp -m tcp --dport 443 -j REDIRECT --to-ports 8443 Create low permission user to run the web server Avoid running any custom code or the web server as a high permission user. A security...
Read More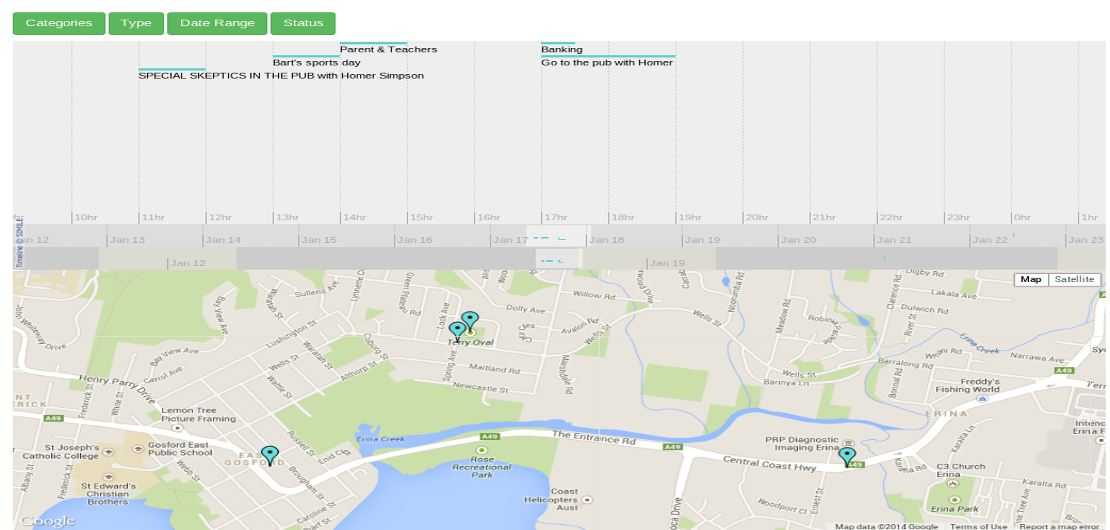
What is the new Timeline module?
23 Jan 2014
Timeline is more than a graphical representation of your JobTrack data, it is interactive allowing you to link back to the item with a click to see the full details, edit and add details. Select from the filters to change the date range and items displayed according to type, category and status. Items are tasks, events or sales opportunities which have been entered and scheduled to a day and time. You'll see items in timeline bands with a colour line representing their scheduled time and duration...
Read More
How do I send out event invitations?
16 Jan 2014
Create a new event. Invite your contacts by selecting the tab 'Invite Others' Send the invitation via email Press the button "Send Invitation" to create an email populated with your contacts. The email opens up with a pre defined template that can be changed. Sample invitation Your contact will receive an email that contains the options to accept your invitation or reject it. When the recipient presses "accept" or "reject" links on your invitation, the system will update the the attendee confirmation...
Read More
Page Keywords Meta Tag
8 Jan 2014
The "keywords" meta tags is no longer used by any of the major search engines. Under some circumstances they can actually be scored negatively against the page rank, when a high count of irrelevant or duplicated key words are added. The system will automatically de-duplicate keywords if entered. For example if "SEO, meta, Seo,tags,,," is entered as the list of keywords, the list will be converted to "SEO, meta, tags" Later releases will deprecate the entry of key words completely. Currently Google...
Read More
Assigning a domain (host) name to your stSoftware hosted website or web system
1 Jan 2014
After you have registered a new domain name with a domain name (DNS) provider such goDaddy, or you have an exisiting domain name, you need to change the associated IP address so that your domain name points to stSoftware's servers. Or contact us to add "Assigning your domain name" service to your website or websystem package and we'll manage it for you. Assign your domain (host) name to the IP addresses of our servers Have your DNS pointed to either of the two groupings of IP addresses below; 101...
Read More
What is Web Forms?
20 Dec 2013
stSoftware's Forms is a web based designer stSoftware's Forms is a web based designer that enables web forms to be created quickly and easily. Forms can then be consumed on most common mobile devices from the internet, anywhere and anytime. stSoftware's Forms are integrated with stSoftware's Workflow to automate business processes and deliver rich cloud applications. Quick and Easy Forms Design Empower business users and enhance developer productivity: Auto-generate forms to support your business...
Read More
HTML component accessibility validation
18 Dec 2013
When a HTML component is changed validations for the validity and for accessibility will be performed.
Read More
Check your articles,email & pages Accessibility
18 Dec 2013
HTML code in the rich text editor to be checked click the Check Accessibility button to check Check results in another browser window
Read More
How to configure DNS round robin for web server failover?
18 Dec 2013
Server Cluster A cluster of servers (two or more ) can be setup and the DNS entry for your site can be defined with the IP addresses for each of the servers, this is known as Round-robin DNS DNS round-robin for Web server failover www1 -> 10.0.0.1 www2 -> 10.0.0.2 www -> 10.0.0.1, 10.0.0.2 Now the DNS server returns both IP addresses for each www query, in random order. If both web servers are up, obviously no problem. If one is down. the questions are, will the browser try the second IP address...
Read More